Identity Broker Forum
Welcome to the community forum for Identity Broker.
Browse the knowledge base, ask questions directly to the product group, or leverage the community to get answers. Leave ideas for new features and vote for the features or bug fixes you want most.

 Minimal AD delegate rights for UNIFYBroker/Active Directory service account
Minimal AD delegate rights for UNIFYBroker/Active Directory service account
I do not want to give more permission than that is needed (i.e. no Domain Admin right). Hence please advise the minimal AD delegate rights that the UNIFYBroker service account requires to:
- Create new users
- Modify attribute of an existing users
- Move users from one OU to another
- Suspend/activate an user (userAccountControl)
- Set initial password and set users must change password in the next logon
- Reset/ change password for an existing user
Thanks

Hi Huu,
As you’re probably aware, AD permissions can get extremely complicated and can be done in a number of ways. For example, the topic on Implementing Least-Privilege Administrative Models is a 40 minute read - and it merely introduces the concepts and references countless other articles.
The approach that we recommend for Active Directory is to provide the use cases to the Active Directory administrator - so that they can create an account with least-privileges that works within their security model framework. As with all connectors, if this information can be condensed into a common set of recommendations, we would include this information in our documentation as either a set of prerequisites or as options/guidelines.
Thanks.

 AD Connector One LDAP Modify failed transaction makes all subsequent transaction failed ...
AD Connector One LDAP Modify failed transaction makes all subsequent transaction failed ...
Refer to few thousand of repeating error in the log\
20180803,05:38:08,UNIFY Identity Broker,Connector,Warning,"Update entities to connector failed.
Update entities [Count:3215] to connector AD Users failed with reason Received error code EntryAlreadyExists for item with dn CN=redacted,DC=au. Message: 00002071: UpdErr: DSID-031B0B87, problem 6005 (ENTRY_EXISTS), data 0
. Duration: 00:00:09.5226690
Error details:
System.Exception: Received error code EntryAlreadyExists for item with dn CN=redacted,DC=au. Message: 00002071: UpdErr: DSID-031B0B87, problem 6005 (ENTRY_EXISTS), data 0
---> System.DirectoryServices.Protocols.DirectoryOperationException: The object exists. Server stack trace:
at System.DirectoryServices.Protocols.LdapConnection.ConstructResponse(Int32 messageId, LdapOperation operation, ResultAll resultType, TimeSpan requestTimeOut, Boolean exceptionOnTimeOut)
at System.Runtime.Remoting.Messaging.StackBuilderSink._PrivateProcessMessage(IntPtr md, Object[] args, Object server, Object[]& outArgs)
at System.Runtime.Remoting.Messaging.StackBuilderSink.AsyncProcessMessage(IMessage msg, IMessageSink replySink) Exception rethrown at [0]:
at System.DirectoryServices.Protocols.LdapConnection.EndSendRequest(IAsyncResult asyncResult)
at System.Threading.Tasks.TaskFactory`1.FromAsyncCoreLogic(IAsyncResult iar, Func`2 endFunction, Action`1 endAction, Task`1 promise, Boolean requiresSynchronization)
--- End of stack trace from previous location where exception was thrown ---
at System.Runtime.CompilerServices.TaskAwaiter.ThrowForNonSuccess(Task task)
at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
at System.Runtime.CompilerServices.TaskAwaiter`1.GetResult()
at Unify.Connectors.AD.ADAgent.<ErrorCheckRequest>d__24`1.MoveNext()
--- End of inner exception stack trace ---
at Unify.Framework.Auditing.AuditingExtensions.<>c__DisplayClass4_0.<TaskContinueWithExceptionPassthough>b__0(Task t)
at System.Threading.Tasks.Task.Execute()
--- End of stack trace from previous location where exception was thrown ---
at System.Runtime.CompilerServices.TaskAwaiter.ThrowForNonSuccess(Task task)
at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
at Unify.Product.IdentityBroker.EventNotifierUpdatingAsyncConnectorDecorator.<UpdateEntitiesAsync>d__3.MoveNext()",Normal
20180803,05:38:08,UNIFY Identity Broker,EntitySaver,Error,"The entity 546564 (e5b5ef1a-46df-4751-9878-e3a8e8fff5c8) for the adapter AD User Adapter (9f73e5e5-30df-4142-b850-db3e31f0a931) failed to update for the following reasons: Received error code EntryAlreadyExists for item with dn CN=redacted,DC=au. Message: 00002071: UpdErr: DSID-031B0B87, problem 6005 (ENTRY_EXISTS), data 0
",Normal
20180803,05:38:08,UNIFY Identity Broker,EntitySaver,Error,"The entity 603085 (b108073b-e6f1-4ffb-8d9b-02c23f7c1efa) for the adapter AD User Adapter (9f73e5e5-30df-4142-b850-db3e31f0a931) failed to update for the following reasons: Received error code EntryAlreadyExists for item with dn CN=redacted,DC=au. Message: 00002071: UpdErr: DSID-031B0B87, problem 6005 (ENTRY_EXISTS), data 0
",Normal

This dll adds back in the patch from some time ago: Unify.Connectors.AD.dll

 Allow configuration of Search Scope for Active Directory connector
Allow configuration of Search Scope for Active Directory connector
From How to filter sub-OUs in AD connector, it would be nice if you could configure the search scope for the Active Directory connector, which is currently hard-coded to Subtree.

 accountExpires in AD User Connector
accountExpires in AD User Connector
How can I retrieve accountExpires field in AD User Connector? I could not find the field in the schema provider but LDP search shows it.
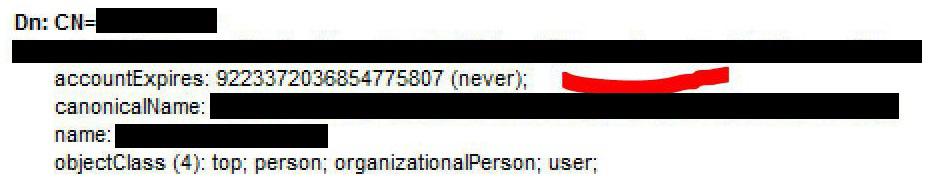
I manually added the field into schema, trying with different types: Date, Timestamp, Long but Import All does not return any value.

Hi Huu,
It should be importable as "accountExpires" as a Timestamp. However, the value will not be set on the entity for "never".

 How to filter sub-OUs in AD connector
How to filter sub-OUs in AD connector
An AD connector will search objects in an OU in sub-tree mode. This means it looks through all sub-OUs.
What to do if only objects in few selected sub-OUs need to be imported? i.e.
Based Container: OU=User, DC=company, DC=com
only objects in 2 sub-OU needed to be import:
OU=Staff,OU=User, DC=company, DC=com
OU=Disabled_Staff,OU=User, DC=company, DC=com

 Incorrect Error Reporting in AD Connector OU Misconfiguration
Incorrect Error Reporting in AD Connector OU Misconfiguration
When the Object Container is misconfigured in an AD Connector the error that you get does not describe the issue. The error you get is something like
"System.FormatException: Index (zero based) must be greater than or equal to zero and less than the size of the argument list."
when it should be something like "
System.Exception: Received error code NoSuchObject. Message: 0000208D: NameErr: DSID-03100238, problem 2001 (NO_OBJECT), data 0, best match of:
'DC=contosso,DC=com'
---> System.DirectoryServices.Protocols.DirectoryOperationException: The object does not exist.
"

 Unable to write data to the transport connection
Unable to write data to the transport connection
The above exception was logged earlier this morning in the IdB log. I only noticed this because the adapter was RED on the IdB dashboard during an export operation, and I decided to search the logs. Initially my search for "exception" found nothing, but a subsequent search for "error" returned this from 3:25 am this morning:
Handling of LDAP change log request. Handling of LDAP change log request from user MIM_IDBMA on connection 127.0.0.1:65355 failed with error "Unable to write data to the transport connection: An established connection was aborted by the software in your host machine.". Duration: 00:08:13.5165781.
I was actually following up on another older error from November, and otherwise would not have noticed this problem. Interestingly there was evidence an hour earlier of a data inconsistency in the CORP AD forest which since seems to have been resolved (AD enforces uniqueness of UPN, so I can't understand how the IdB adapter could be complaining of duplicate DNs when the DN is derived from an enforced unique attribute - unless there is a timing issue due to the processing of deltas such that there is a problem after a rename until the next connector full import removes a duplicate):
Handling of LDAP change log request. Handling of LDAP change log request from user MIM_IDBMA on connection 127.0.0.1:60870 failed with error "Found multiple entities with the distinguished name 'CN=servicio@pr.qbe.com,OU=LicensedUsers,DC=IdentityBroker'.". Duration: 00:00:01.2500019.
I am only speculating that this export error had something to do with the adapter integrity issue which appears to be due to a shortcoming of the delta processing logic.
I am also now wondering if this exception may be leading to others as a result of compromised integrity.
Extract from log as follows:
20170612,17:25:02,UNIFY Identity Broker,Adapter,Information,"Request to reflect change entities of the adapter. Request to reflect change entities of the AAD User Licensing (03228c30-2401-41a9-9977-57a75423829c) adapter completed with 0 adds, 31 updates and 0 deletes across 1 pages. Duration: 00:05:07.2662214",Normal 20170612,17:25:02,UNIFY Identity Broker,LDAP engine,Error,"Handling of LDAP change log request. Handling of LDAP change log request from user MIM_IDBMA on connection 127.0.0.1:65355 failed with error ""Unable to write data to the transport connection: An established connection was aborted by the software in your host machine."". Duration: 00:08:13.5165781.",Normal 20170612,17:25:02,UNIFY Identity Broker,LDAP engine,Information,"Handling of LDAP change log request. Handling of LDAP change log request from user MIM_IDBMA on connection 127.0.0.1:65534 completed successfully. Added: 0. Modified: 0. Renamed: 0. Deleted: 1. Total: 1. Duration: 00:03:01.7347333.",Normal 20170612,17:25:03,UNIFY Identity Broker,Change detection engine,Information,"Change detection engine import changes started. Change detection engine import changes for connector CORP AD Group started.",Normal 20170612,17:25:03,UNIFY Identity Broker,Connector,Information,"Request to import changes from connector. Request to import changes from connector CORP AD Group.",Normal 20170612,17:25:03,UNIFY Identity Broker,Connector,Information,"Import changes from connector completed. Import changes from connector CORP AD Group reported 0 changes. Duration: 00:00:00",Normal 20170612,17:25:03,UNIFY Identity Broker,Change detection engine,Information,"Change detection engine import changes completed. Change detection engine import changes for connector CORP AD Group returned 0 possible changes. Duration: 00:00:00.5000092",Normal 20170612,17:25:05,UNIFY Identity Broker,Adapter,Information,"Request to reflect change entities of the adapter. Request to reflect change entities of the AAD User Licensing (03228c30-2401-41a9-9977-57a75423829c) adapter completed with 0 adds, 21 updates and 0 deletes across 1 pages. Duration: 00:00:00.2967598",Normal
Using: UNIFY Identity Broker Management Studio, v5.0.5 Revision #0
Using Plugin:
| Microsoft Active Directory | 5.0.1.2 |

Hi Bob,
The error
Handling of LDAP change log request from user MIM_IDBMA on connection 127.0.0.1:65355 failed with error "Unable to write data to the transport connection: An established connection was aborted by the software in your host machine.". Duration: 00:08:13.5165781.
indicates that upon completing the handling of a changelog request, Identity Broker found that the LDAP connection was dropped by the client. Given that the duration of the operation is over 8 minutes, I'm assuming that this is exceeding your timeout.
The long duration could be caused by high activity on the Identity Broker server. You could try increasing the timeout, but if the issue is resolving itself (activity dropping and subsequent imports succeeding) then perhaps leaving the connections to timeout is the best solution to prevent the client blocking downstream processing during these busy periods.
I don't believe this is related to the duplicate DNs. Have you checked the entity context, from the UI or from SQL, to check for the duplicate DNs?

 Test setting initial password and enabling account
Test setting initial password and enabling account
Test to confirm that Identity Broker for Microsoft Active Directory is capable of provisioning users in an enabled state. A few things we know:
- SSL must be enabled in AD and on the connection;
- The password must meet the complexity requirements;
- User userAccountControl to enable the account;
- If using unicodePwd there are some prerequisites for the format of the password (enclosed in quotes and base64 encoded);
Other:
- Is anything logged in AD/Windows event log that can help diagnose?
- Can the traffic be traced?
- Is there another password field that gets the outcome without having to use unicodePwd?
- Do we have to change the connector to make this easier?

 Identity Broker for Microsoft Active Directory - ability to use SSL with certificate that doesn't match endpoint address
Identity Broker for Microsoft Active Directory - ability to use SSL with certificate that doesn't match endpoint address
CloudBroker requires the following:
- SSL on all communication
IDBAD will fail if the end-point address (a public DNS entry) is different to the certificate supplied by the AD end-point, something that is entirely likely to happen if a customer cannot use their NAT to set up SSL and terminate at that address. For example:
IDBAD is set to connect to unify-demo-idbchrslite-1-ad.cloudapp.net, however the AD certificate is issued by the domain CA which makes the certificate idbpc21-ad.demo.unifysolutions.net.
The AD connector should permit the certificate to be determined by a name in the our configuration. The certificate must still be valid against the local machine certificate store.

 AD connector - add filter to display UI
AD connector - add filter to display UI
The filter that is part of the AD query is missing from the display UI component. It should be added.
2015-04-30 11_22_46-AD Connector - UNIFY Identity Broker.png
Customer support service by UserEcho

